Virtru Data Protection Platform Bot
The Virtru Data Protection Platform Bot enables your organization to include the most sensitive and regulated data in your automation workflow.
Top Benefits
- Immediately take control of your data and enhance your existing security investments.
- Easily secure data as it is created and shared within and outside your organization.
- Collaborate with confidence while maintaining visibility and control of data.
- Split knowledge key management, host your own keys and HSM support.
Tasks
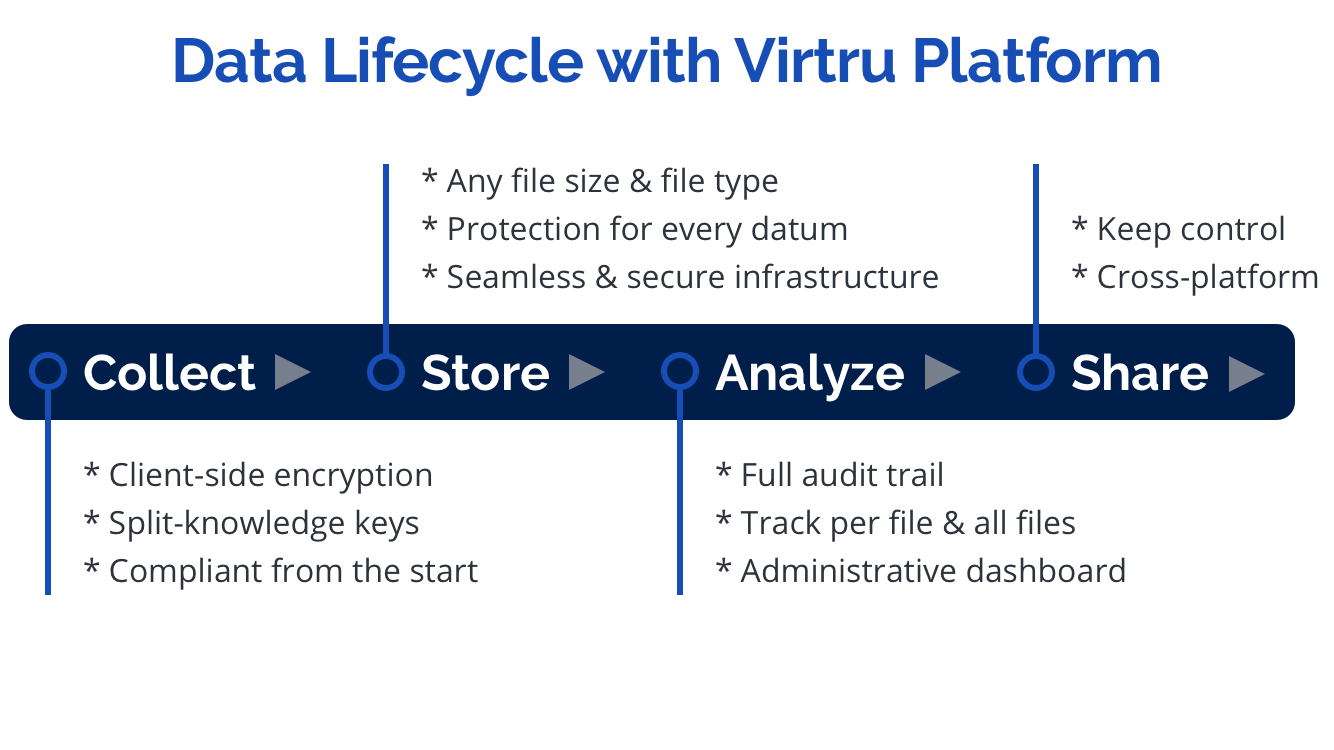
- Persistent data protection through encryption, policy management, and access control.
- Share securely across platforms and devices.
- Revoke access, control forwarding, watermark, and persistent universal access formats.
- Visibility into where your data is and how it is being used via audit.
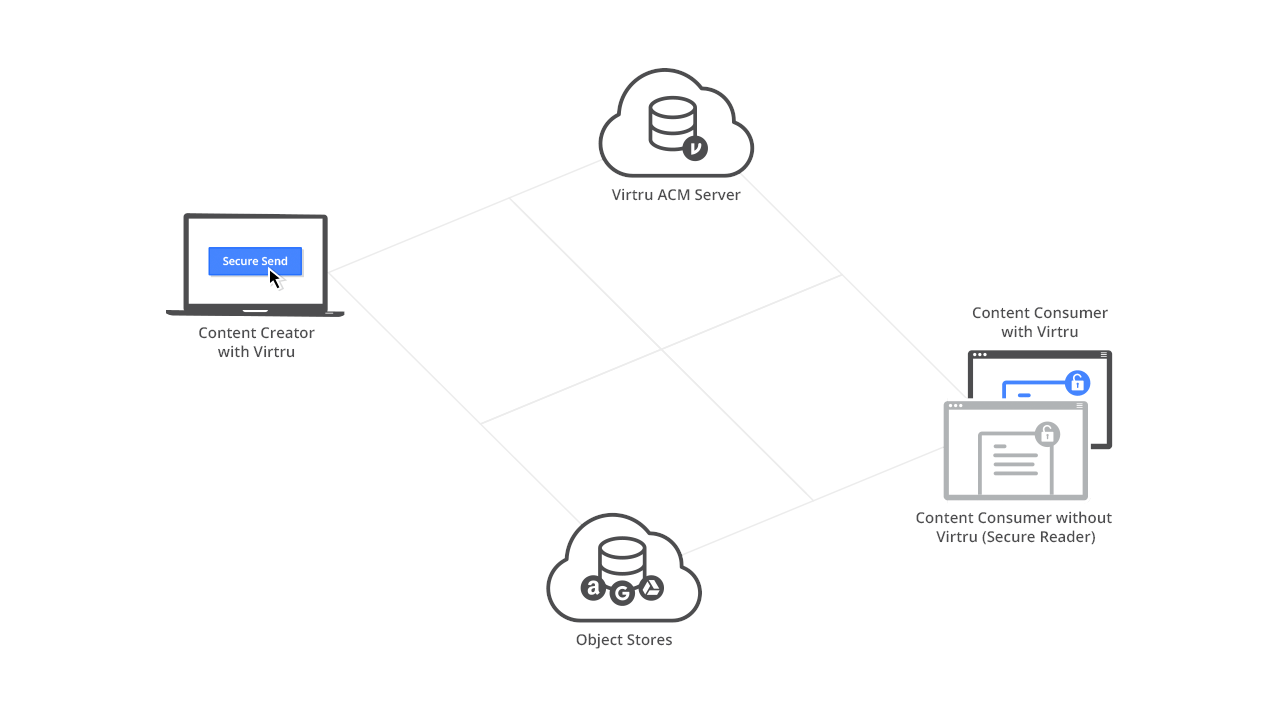
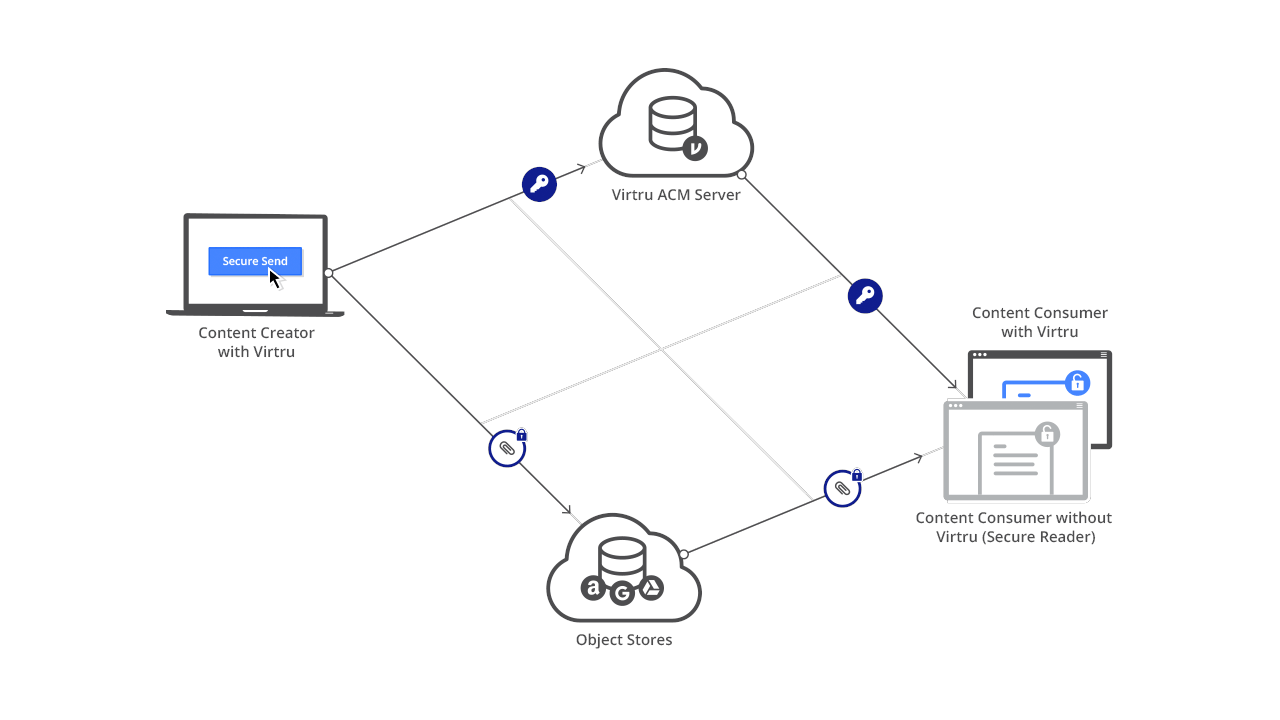
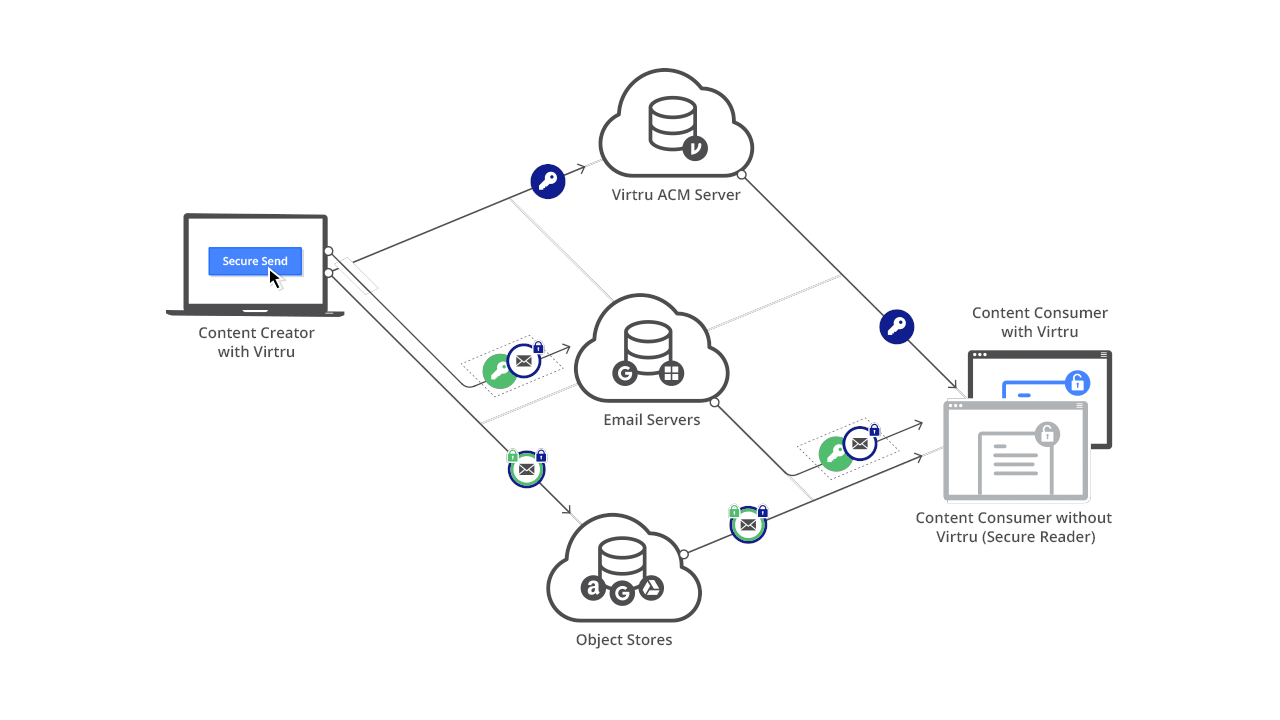
The Virtru Platform infrastructure enables Virtru and third-party developers to embed end-to-end encryption, granular access controls, and key management capabilities into applications and workflows to prevent unauthorized access and ensure data privacy.
Virtru employs a split knowledge architecture that stores encrypted content separately from the encryption keys protecting it, supporting a Zero Trust framework where all system components are continuously authenticated, verified, and authorized.
Only authorized entities can access unencrypted content. Virtru can never access unencrypted content or decrypt user content outside of customer-controlled Virtru clients: When we have the keys, we cannot access the content, and when we have the encrypted content, we can’t access the keys to decrypt and access it.
Free
- Applications
-

- Business Process
- Information Technology
- Category
- CollaborationSecurityUtility
- Downloads
- 22
- Vendor
- Automation Type
- Bot
- Last Updated
- December 11, 2020
- First Published
- April 16, 2020
- Platform
- 11.3
- Community Version
- 11.3.1
- ReadMe
- ReadMe
- End User License Agreement
- EULA
- Support
-
- Virtru
- Mon, Tue, Wed, Thu, Fri 9:00-17:00 UTC+0
- 2404186027
- support@virtru.com
- Agentic App Store FAQs
- Bot Security Program
-
 Level 1
Level 1
Setup Process
Install
Download the Bot and follow the instructions to install it in your AAE Control Room.
Configure
Open the Bot to configure your username and other settings the Bot will need (see the Installation Guide or ReadMe for details.)
Run
That's it - now the Bot is ready to get going!
Requirements and Inputs
- Encryption Inputs: Source File, Target File, Owner Email, Authentication Key
- Decryption Inputs: Source File, Target File, Owner Email, Authentication Key